AZ-500 Online Practice Questions and Answers
References: https://docs.microsoft.com/en-us/xamarin/xamarin-forms/data-cloud/cosmosdb/authentication
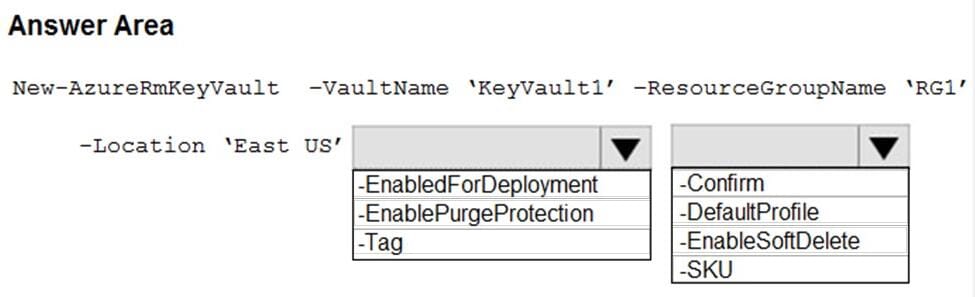
You need to create an Azure key vault. The solution must ensure that any object deleted from the key vault be retained for 90 days.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
SIMULATION You need to ensure that the events in the NetworkSecurityGroupRuleCounter log of the VNET01-Subnet0-NSG network security group (NSG) are stored in the logs11597200 Azure Storage account for 30 days.
To complete this task, sign in to the Azure portal.
A. See the explanation below.
You have an Azure SQL Database server named SQL1.
You plan to turn on Advanced Threat Protection for SQL1 to detect all threat detection types.
Which action will Advanced Threat Protection detect as a threat?
A. A user updates more than 50 percent of the records in a table.
B. A user attempts to sign as select * from table1.
C. A user is added to the db_owner database role.
D. A user deletes more than 100 records from the same table.
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry.
What should you create?
A. a secret in Azure Key Vault
B. a role assignment
C. an Azure Active Directory (Azure AD) user
D. an Azure Active Directory (Azure AD) group
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant.
When a developer attempts to register an app named App1 in the tenant, the developer receives the error message shown in the following exhibit.
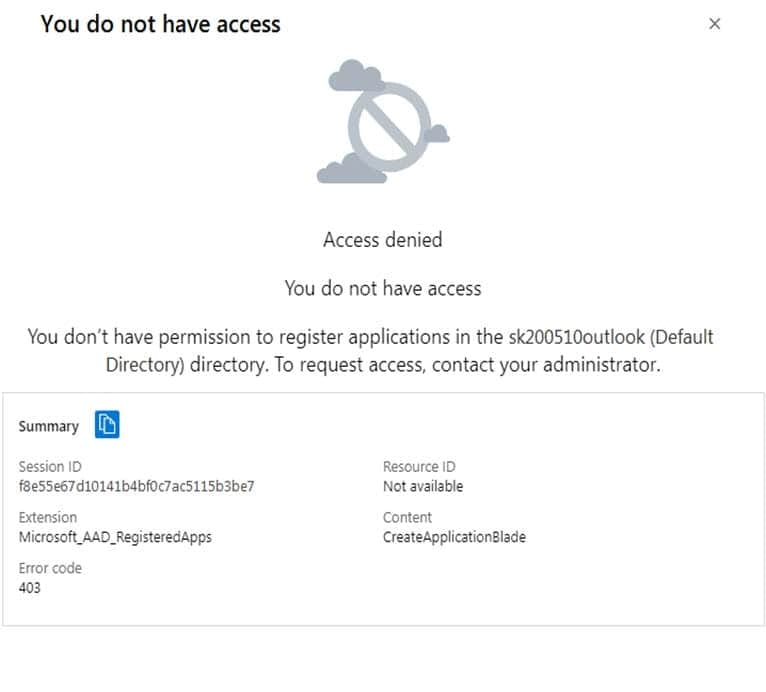
You need to ensure that the developer can register App1 in the tenant. What should you do for the tenant?
A. Modify the User settings
B. Set Enable Security default to Yes.
C. Modify the Directory properties.
D. Configure the Consent and permissions settings for enterprise applications.
A support engineer plans to perform several Azure management tasks by using the Azure CLI.
You install the CLI on a computer.
You need to tell the support engineer which tools to use to run the CLI.
Which two tools should you instruct the support engineer to use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Command Prompt
B. Azure Resource Explorer
C. Windows PowerShell
D. Windows Defender Firewall
E. Network and Sharing Center
You make use of Azure Resource Manager templates to deploy Azure virtual machines.
You have been tasked with making sure that Windows features that are not in use, are automatically inactivated when instances of the virtual machines are provisioned.
Which of the following actions should you take?
A. You should make use of Azure DevOps.
B. You should make use of Azure Automation State Configuration.
C. You should make use of network security groups (NSG).
D. You should make use of Azure Blueprints.
Your company's Azure subscription includes an Azure Log Analytics workspace.
Your company has a hundred on-premises servers that run either Windows Server 2012 R2 or Windows Server 2016, and is linked to the Azure Log Analytics workspace. The Azure Log Analytics workspace is set up to gather performance
counters associated with security from these linked servers.
You have been tasked with configuring alerts according to the information gathered by the Azure Log Analytics workspace.
You have to make sure that alert rules allow for dimensions, and that alert creation time should be kept to a minimum. Furthermore, a single alert notification must be created when the alert is created and when the alert is sorted out.
You need to make use of the necessary signal type when creating the alert rules.
Which of the following is the option you should use?
A. You should make use of the Activity log signal type.
B. You should make use of the Application Log signal type.
C. You should make use of the Metric signal type.
D. You should make use of the Audit Log signal type.
You need to consider the underlined segment to establish whether it is accurate.
Your Azure Active Directory Azure (Azure AD) tenant has an Azure subscription linked to it.
Your developer has created a mobile application that obtains Azure AD access tokens using the OAuth 2 implicit grant type.
The mobile application must be registered in Azure AD.
You require a redirect URI from the developer for registration purposes.
Select “No adjustment required” if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
A. No adjustment required
B. a secret
C. a login hint
D. a client ID
You have an Azure subscription that uses Microsoft Sentinel.
You need to create a Microsoft Sentinel notebook that will use the Guided Investigation - Anomaly Lookup template.
What should you create first?
A. an analytics rule
B. a Log Analytics workspace
C. an Azure Machine Learning workspace
D. a hunting query


