500-220 Online Practice Questions and Answers
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
A. Controller disconnection behavior
B. Captive Portal strength
C. Simultaneous logins
D. Firewall and traffic shaping
E. RADIUS for splash page settings
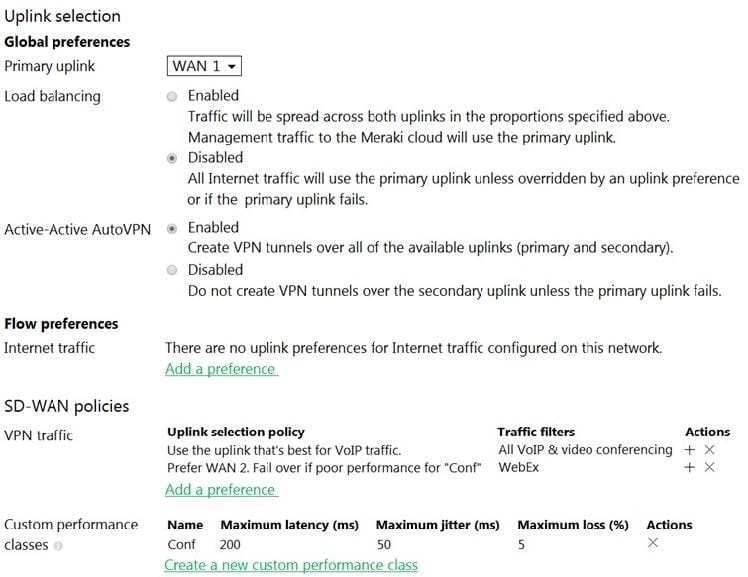
Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
A. WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the "Conf" performance class.
B. WebEx traffic will prefer WAN 1 as it is the primary uplink.
C. WebEx traffic will prefer WAN 2 as long as it is up.
D. WebEx traffic will be load-balanced between both active WAN links.
Which two primary metrics does Meraki Insight use to calculate the Application Performance Score? (Choose two.)
A. Maximum Jitter
B. Total Bandwidth Usage
C. Maximum Latency
D. Per-flow Goodput
E. Application Response Time
What are two organization permission types? (Choose two.)
A. Full
B. Read-only
C. Monitor-only
D. Write
E. Write-only
What are two roles of the network and device tags in a Dashboard? (Choose two.)
A. Tags enable administrators to configure a combination of network and device specific tags to create summary reports filtered for specific devices across multiple networks.
B. Network tags can be used to assign networks to separate Auto VPN domains in an Organization with many networks.
C. Network tags can be used to simplify the assignment of network-level permissions in an Organization with many networks.
D. Device tags can be used to simplify the assignment of device-level permissions in an Organization with many administrators.
E. Device tags can be assigned to MR APs to influence the gateway selection for repeaters in a mesh wireless network.
A customer wants to use Microsoft Azure to host corporate application servers.
Which feature does the customer get by using a vMX appliance rather than connecting directly to Azure by VPN?
A. malware protection
B. SD-WAN
C. next-generation firewall
D. intrusion prevention
Which type of authentication protocol is used when using OSPF on an MX appliance?
A. MD5
B. certificate
C. plaintext
D. SHA-1
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
A. Content filtering
B. Bridge mode
C. 802.11r
D. Dual band operating with Band Steering
Which Cisco Meraki product must be deployed in addition to Systems Manager so that Systems Manager Sentry enrollment can be used?
A. MS Switch
B. Meraki Insight
C. MR Access Point
D. MV Smart Camera
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
A. No configuration step is necessary; automatic updating is the default behavior.
B. Configure automatic updating of iOS devices in the Meraki installed profile.
C. Create a security policy that enables automatic updates.
D. Create a profile with automatic update enabled and apply it to iOS devices.

