400-007 Online Practice Questions and Answers
Which main IoT migration aspect should be reviewed for a manufacturing plant?
A. Sensors
B. Security
C. Applications
D. Wi-Fi Infrastructure
E. Ethernet Switches
Refer to the diagram.
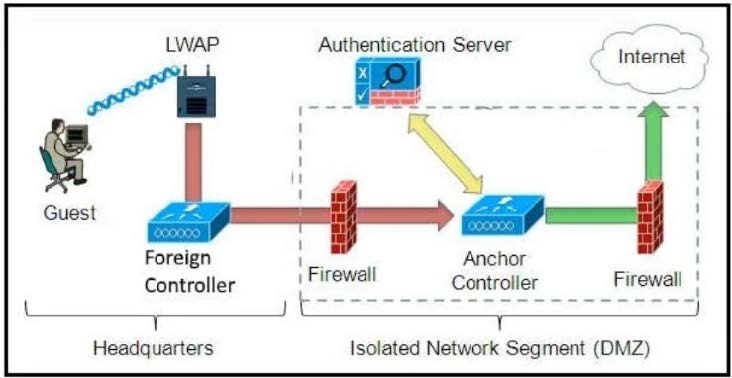
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
A. Send packets from the foreign controller to the anchor controller via Layer 3 MPLS VPN or VRF-Lite
B. Send packets without encapsulation to the anchor controller over the routed network.
C. Encapsulate packets into an EoIP tunnel and send them to the anchor controller.
D. Send packets from the foreign controller to the anchor controller via IPinIP or IPsec tunnel.
An existing wireless network was designed to support data traffic only. You must now install context Aware services for location tracking changes must be applied to the existing wireless network to increase the location accuracy? (Chose two)
A. Add access points along the perimeter of the coverage area.
B. Increase the access point density to create an average inter-access point distance of less than 40 feet or 12.2 meters
C. Use directional antennas to provide more cell overlapping
D. Install additional access points in monitor mode where the co-channel interference would otherwise be affected
E. Fine tune the radio configuration of the access point to have a higher average transmission power to achieve better coverage
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
A. Ensure that strong cryptography is applied for users who have administrative access through networks
B. Apply strong cryptography and security protocols to safeguard sensitive cardholder data.
C. Apply strong encryption for transmission of cardholder data across public networks.
D. Protect all user systems against malware and frequently update antivirus software
E. Maintain a policy that addresses information security for employees and third parties.
Refer to the exhibit.
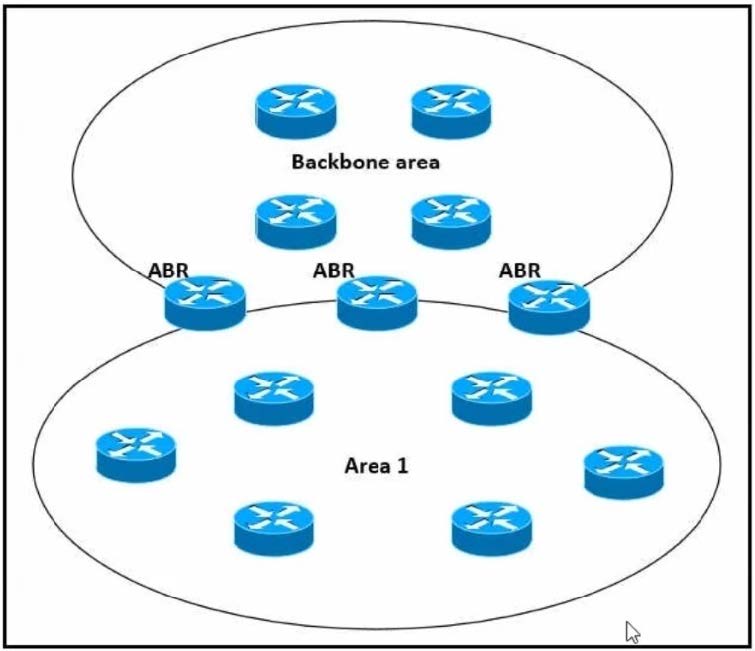
Which impact of using three or more ABRs between the backbone area and area 1 is true?
A. In a large-scale network LSA replication by all ABRs can cause serious scalability issues
B. Multiple ABRs reduce the CPU processing on each A6R due to splitting prefix advertisement
C. In a large-scale network multiple ABRs can create microloops.
D. Prefixes from the non-backbone area are advertised by one ABR to the backbone
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
A. system-oriented architecture
B. OSASE architecture
C. platform-oriented architecture
D. SASE architecture
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
A. workload
B. work domain
C. workplace
D. workgroup
E. workspace
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.)
A. Cisco Prime Service Catalog
B. Cisco Open Virtual Switch
C. Cisco Nexus switches
D. Cisco UCS
E. Cisco Open Container Platform
F. Cisco Virtual Network Function
Refer to the exhibit.
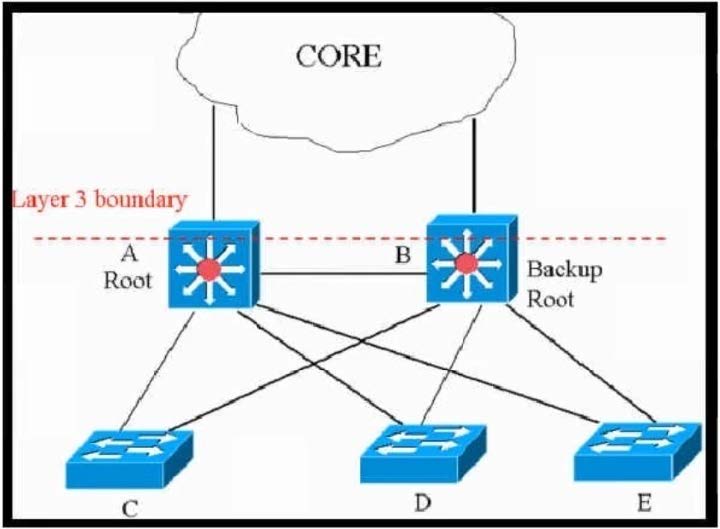
This network is running legacy STP 802.1 d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
A. Only the maximum_transmission_halt_delay and diameter parameters are configurable parameters in 802.1d to speed up STP convergence process.
B. The max_age and forward delay parameters can be adjusted to speed up STP convergence process.
C. The transit_delay=5 and bpdu_delay=20 are recommended values, considering hello_timer=2 and specified diameter.
D. Only the transit_delay and bpdu_delay timers are configurable parameters in 802.1d to speed up STP convergence process.
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
A. Control Plane Protection host subinterface
B. Control Plane Protection main interface
C. Control Plane Protection transit subinterface
D. Control Plane Protection CEF-exception subinterface

