352-001 Online Practice Questions and Answers
Refer to the exhibit.
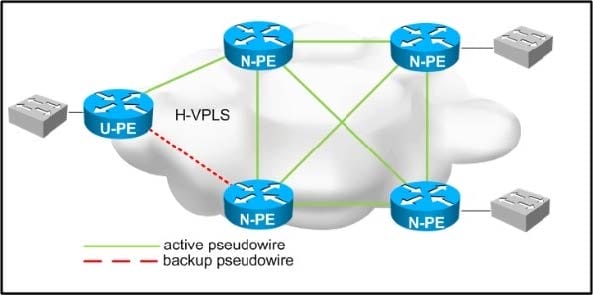
You are designing a loop-free hierarchical VPLS service. Which two design considerations should be implemented for the pseudowires between the N-PE and U-PE routers? (Choose two.)
A. Disable split horizon toward the N-PE routers.
B. Disable split horizon toward the U-PE router.
C. Enable split horizon toward the U-PE router.
D. Enable split horizon toward the N-PE routers.
E. Disable MAC learning on the U-PE route.
F. Disable MAC learning on the N-PE routers.
Your company is designing a service provider network management solution in which customers are billed for 95th percentile network utilization. The service provider requires that an IETF standard be utilized to collect the data. Which method should be used to collect the data?
A. IPFIX
B. NETFLOW
C. RMON
D. IPFLOW
E. NBAR
A service provider wants to maximize forwarding memory, routing memory, and CPU resources on PE devices for enterprise customers that have very few sites (two to three) and a large number of prefixes (several thousand).
Which service should the service provider offer these customers?
A. VPWS
B. VPLS
C. L3VPNs (RFC 2547-based)
D. InterAS L3VPN
You are designing the QoS features for a large enterprise network that includes DMVPN. When would you need to configure QoS preclassify?
A. when you are marking packets with the DSCP bits
B. when you are marking packets with the TOS bits
C. when your service provider requires the DSCP bits be set
D. when the QoS policy cannot be based on DSCP ToS bits
Which statement is correct about route reflector design?
A. Route reflectors should be placed to find the best exit point from the AS.
B. The EIGRP unequal cost, load-balancing characteristic facilitates route reflector placement.
C. Route reflectors should not be placed on the data path.
D. Route reflectors help find the closest exits from the AS.
Which option should be part of your network design to support dynamic mutual redistribution between multiple OSPFv2 and IS-IS boundaries, to avoid suboptimal routing?
A. route tagging and administrative policies
B. route filtering and administrative policies
C. route aggregation and administrative policies
D. disabling IS-IS wide metrics
You are designing a network virtualization solution across an enterprise campus. The design requirements include the ability to virtualize the data plane and control plane using VLANs and VRFs while maintaining end-to-end logical path transport separation across the network, with access to grouped resources available at the access edge. Your network virtualization design can be categorized as which three primary models? (Choose 3)
A. group virtualization
B. services virtualization
C. edge isolation
D. session isolation
E. path isolation
F. device virtualization
A company decided to replace IEEE 802.1s on the campus and you must propose a Layer 2 open standard technology that is highly scalable, ensures a resilient loop-free switched domain, and allows for utilizing all links in the Layer 2 domain.
Which Layer 2 technology meets these requirements?
A. TRILL
B. VxLAN
C. LACP
D. FabricPath
E. MST
A hosted service provider is designing an IPS solution to protect its DMZ segment. The goal is to detect and prevent anomalous activities and, at the same time, give the security operations team visibility into any attempted attacks against the organization. Which IPS solution should you deploy in the Internet perimeter to accomplish this goal?
A. Deploy IPS as inline mode between the firewall and the servers
B. Deploy IPS as promiscuous mode between the firewall and the servers
C. Deploy IPS as inline mode between the firewall and the internet gateway
D. Deploy IPS as promiscuous mode between the firewall and the internet gateway
Which IEEE standard is commonly used at the data link layer for an access network, in an IoT environment?
A. Wireless Regional Area Network
B. Low-Rate Wireless Network
C. Wireless Local Area Network
D. Broadband wireless metropolitan Network


