350-201 Online Practice Questions and Answers
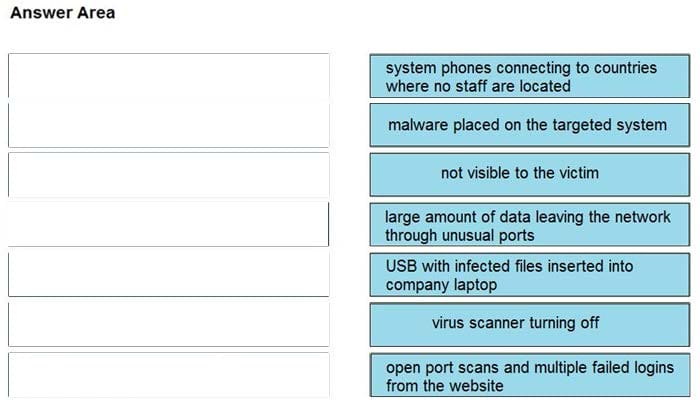
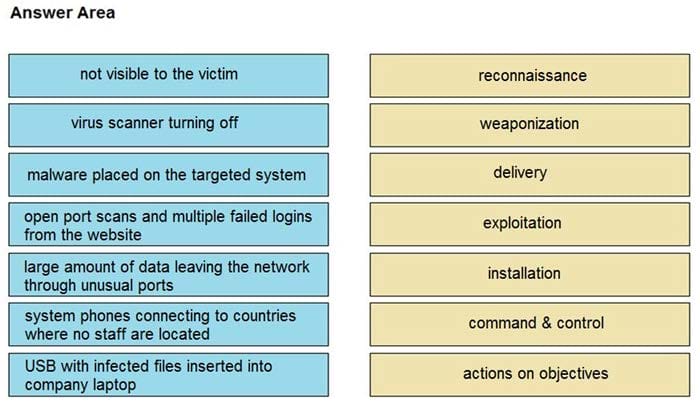
DRAG DROP
Drag and drop the type of attacks from the left onto the cyber kill chain stages at which the attacks are seen on the right.
Select and Place:
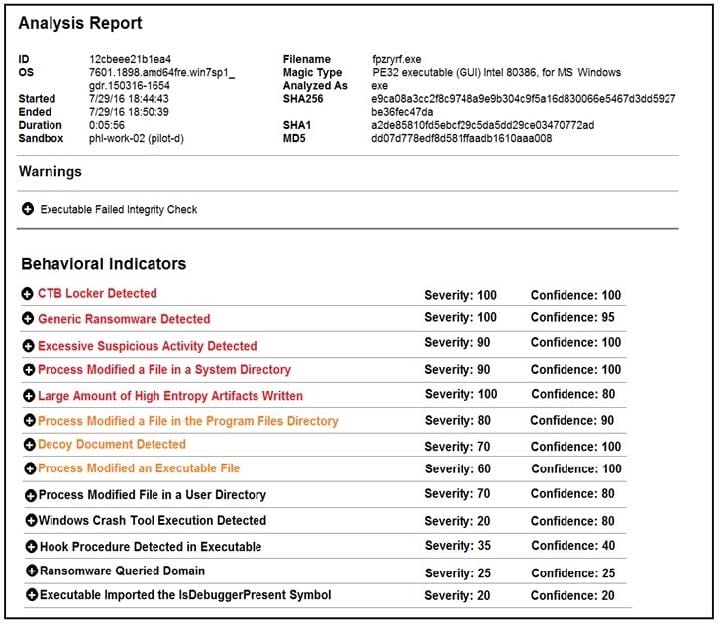
Refer to the exhibit. Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded from this report?
A. The prioritized behavioral indicators of compromise do not justify the execution of the "ransomware" because the scores do not indicate the likelihood of malicious ransomware.
B. The prioritized behavioral indicators of compromise do not justify the execution of the "ransomware" because the scores are high and do not indicate the likelihood of malicious ransomware.
C. The prioritized behavioral indicators of compromise justify the execution of the "ransomware" because the scores are high and indicate the likelihood that malicious ransomware has been detected.
D. The prioritized behavioral indicators of compromise justify the execution of the "ransomware" because the scores are low and indicate the likelihood that malicious ransomware has been detected.
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20 of its hosted applications. Based on the audit, which recommendation should an engineer make for patching?
A. Identify the business applications running on the assets
B. Update software to patch third-party software
C. Validate CSRF by executing exploits within Metasploit
D. Fix applications according to the risk scores
An organization is using a PKI management server and a SOAR platform to manage the certificate lifecycle. The SOAR platform queries a certificate management tool to check all endpoints for SSL certificates that have either expired or are nearing expiration. Engineers are struggling to manage problematic certificates outside of PKI management since deploying certificates and tracking them requires searching server owners manually.
Which action will improve workflow automation?
A. Implement a new workflow within SOAR to create tickets in the incident response system, assign problematic certificate update requests to server owners, and register change requests.
B. Integrate a PKI solution within SOAR to create certificates within the SOAR engines to track, update, and monitor problematic certificates.
C. Implement a new workflow for SOAR to fetch a report of assets that are outside of the PKI zone, sort assets by certification management leads and automate alerts that updates are needed.
D. Integrate a SOAR solution with Active Directory to pull server owner details from the AD and send an automated email for problematic certificates requesting updates.
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
A. 401
B. 402
C. 403
D. 404
E. 405
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled "Invoice RE: 0004489". The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
Refer to the exhibit. For IP 192.168.1.209, what are the risk level, activity, and next step?
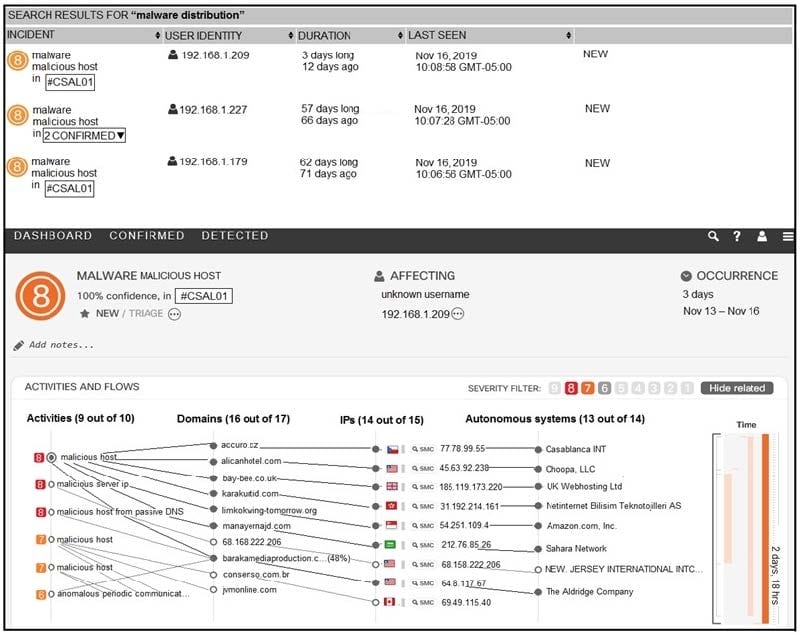
A. high risk level, anomalous periodic communication, quarantine with antivirus
B. critical risk level, malicious server IP, run in a sandboxed environment
C. critical risk level, data exfiltration, isolate the device
D. high risk level, malicious host, investigate further
An analyst wants to upload an infected file containing sensitive information to a hybrid-analysis sandbox. According to the NIST.SP 800-150 guide to cyber threat information sharing, what is the analyst required to do before uploading the file to safeguard privacy?
A. Verify hash integrity.
B. Remove all personally identifiable information.
C. Ensure the online sandbox is GDPR compliant.
D. Lock the file to prevent unauthorized access.
An engineer received an incident ticket of a malware outbreak and used antivirus and malware removal tools to eradicate the threat. The engineer notices that abnormal processes are still occurring in the system and determines that manual intervention is needed to clean the infected host and restore functionality. What is the next step the engineer should take to complete this playbook step?
A. Scan the network to identify unknown assets and the asset owners.
B. Analyze the components of the infected hosts and associated business services.
C. Scan the host with updated signatures and remove temporary containment.
D. Analyze the impact of the malware and contain the artifacts.
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A. Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B. Inform the user by enabling an automated email response when the rule is triggered.
C. Inform the incident response team by enabling an automated email response when the rule is triggered.
D. Create an automation script for blocking URLs on the firewall when the rule is triggered.