312-50V9 Online Practice Questions and Answers
LM hash is a compromised password hashing function. Which of the following parameters describe LM
Hash:?
I ?The maximum password length is 14 characters.
II ?There are no distinctions between uppercase and lowercase.
III ?It's a simple algorithm, so 10,000,000 hashes can be generated per second.
A. I
B. I, II, and III
C. II
D. I and II
An attacker runs netcat tool to transfer a secret file between two hosts.
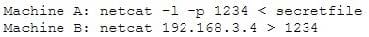
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
A. Machine A: netcat -l -p -s password 1234 < testfile Machine B: netcat
B. Machine A: netcat -l -e magickey -p 1234 < testfile Machine B: netcat
C. Machine A: netcat -l -p 1234 < testfile -pw password Machine B: netcat
D. Use cryptcat instead of netcat
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
A. Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
B. Package the Sales.xls using Trojan wrappers and telnet them back your home computer
C. You can conceal the Sales.xls database in another file like photo.jpg or other files and send it out in an innocent looking email or file transfer using Steganography techniques
D. Change the extension of Sales.xls to sales.txt and upload them as attachment to your hotmail account
_________ is a set of extensions to DNS that provide to DNS clients (resolvers) origin authentication of DNS data to reduce the threat of DNS poisoning, spoofing, and similar attacks types.
A. DNSSEC
B. Zone transfer
C. Resource transfer
D. Resource records
Internet Protocol Security IPSec is actually a suite of protocols. Each protocol within the suite provides different functionality. Collective IPSec does everything except.
A. Protect the payload and the headers
B. Authenticate
C. Encrypt
D. Work at the Data Link Layer
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
A. Perform a vulnerability scan of the system.
B. Determine the impact of enabling the audit feature.
C. Perform a cost/benefit analysis of the audit feature.
D. Allocate funds for staffing of audit log review.
A covert channel is a channel that
A. transfers information over, within a computer system, or network that is outside of the security policy.
B. transfers information over, within a computer system, or network that is within the security policy.
C. transfers information via a communication path within a computer system, or network for transfer of data.
D. transfers information over, within a computer system, or network that is encrypted.
After gaining access to the password hashes used to protect access to a web based application, knowledge of which cryptographic algorithms would be useful to gain access to the application?
A. SHA1
B. Diffie-Helman
C. RSA
D. AES
When setting up a wireless network, an administrator enters a pre-shared key for security. Which of the following is true?
A. The key entered is a symmetric key used to encrypt the wireless data.
B. The key entered is a hash that is used to prove the integrity of the wireless data.
C. The key entered is based on the Diffie-Hellman method.
D. The key is an RSA key used to encrypt the wireless data.
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
A. Teardrop
B. SYN flood
C. Smurf attack
D. Ping of death

