312-50V8 Online Practice Questions and Answers
You've just been hired to perform a pentest on an organization that has been subjected to a large-scale attack. The CIO is concerned with mitigating threats and vulnerabilities to totally eliminate risk.
What is one of the first thing you should to when the job?
A. Start the wireshark application to start sniffing network traffic.
B. Establish attribution to suspected attackers.
C. Explain to the CIO that you cannot eliminate all risk, but you will be able to reduce risk to acceptable levels.
D. Interview all employees in the company to rule out possible insider threats.
This kind of password cracking method uses word lists in combination with numbers and special characters:
A. Hybrid
B. Linear
C. Symmetric
D. Brute Force
Harold is the senior security analyst for a small state agency in New York. He has no other security professionals that work under him, so he has to do all the security-related tasks for the agency. Coming from a computer hardware background, Harold does not have a lot of experience with security methodologies and technologies, but he was the only one who applied for the position. Harold is currently trying to run a Sniffer on the agency's network to get an idea of what kind of traffic is being passed around, but the program he is using does not seem to be capturing anything. He pours through the Sniffer's manual, but cannot find anything that directly relates to his problem. Harold decides to ask the network administrator if he has any thoughts on the problem. Harold is told that the Sniffer was not working because the agency's network is a switched network, which cannot be sniffed by some programs without some tweaking.
What technique could Harold use to sniff his agency's switched network?
A. ARP spoof the default gateway
B. Conduct MiTM against the switch
C. Launch smurf attack against the switch
D. Flood the switch with ICMP packets
While performing data validation of web content, a security technician is required to restrict malicious input. Which of the following processes is an efficient way of restricting malicious input?
A. Validate web content input for query strings.
B. Validate web content input with scanning tools.
C. Validate web content input for type,length,and range.
D. Validate web content input for extraneous queries.
What are the three types of authentication?
A. Something you: know,remember,prove
B. Something you: have,know,are
C. Something you: show,prove,are
D. Something you: show,have,prove
A security analyst in an insurance company is assigned to test a new web application that will be used by clients to help them choose and apply for an insurance plan. The analyst discovers that the application is developed in ASP scripting language and it uses MSSQL as a database backend. The analyst locates the application's search form and introduces the following code in the search input fielD. IMG SRC=vbscript:msgbox("Vulnerable");> originalAttribute="SRC" originalPath="vbscript:msgbox("Vulnerable");>"
When the analyst submits the form, the browser returns a pop-up window that says "Vulnerable".
Which web applications vulnerability did the analyst discover?
A. Cross-site request forgery
B. Command injection
C. Cross-site scripting
D. SQL injection
Jake is a network administrator who needs to get reports from all the computer and network devices on his network. Jake wants to use SNMP but is afraid that won't be secure since passwords and messages are in clear text.
How can Jake gather network information in a secure manner?
A. He can use SNMPv3
B. Jake can use SNMPrev5
C. He can use SecWMI
D. Jake can use SecSNMP
Finding tools to run dictionary and brute forcing attacks against FTP and Web servers is an easy task for hackers. They use tools such as arhontus or brutus to break into remote servers.
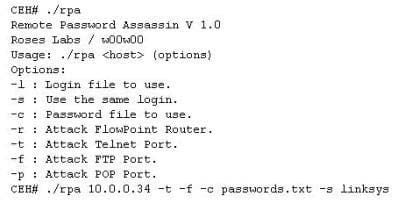
A command such as this, will attack a given 10.0.0.34 FTP and Telnet servers simultaneously with a list of passwords and a single login namE. linksys. Many FTP- specific password-guessing tools are also available from major security sites.
What defensive measures will you take to protect your network from these attacks?
A. Never leave a default password
B. Never use a password that can be found in a dictionary
C. Never use a password related to your hobbies,pets,relatives,or date of birth.
D. Use a word that has more than 21 characters from a dictionary as the password
E. Never use a password related to the hostname,domain name,or anything else that can be found with whois
Attackers send an ACK probe packet with random sequence number, no response means port is filtered (Stateful firewall is present) and RST response means the port is not filtered.
What type of Port Scanning is this?
A. RST flag scanning
B. FIN flag scanning
C. SYN flag scanning
D. ACK flag scanning
Tess King is making use of Digest Authentication for her Web site. Why is this considered to be more secure than Basic authentication?
A. Basic authentication is broken
B. The password is never sent in clear text over the network
C. The password sent in clear text over the network is never reused.
D. It is based on Kerberos authentication protocol

