312-49V10 Online Practice Questions and Answers
Damaged portions of a disk on which no read/Write operation can be performed is known as ______________.
A. Lost sector
B. Bad sector
C. Empty sector
D. Unused sector
Why is it Important to consider health and safety factors in the work carried out at all stages of the forensic process conducted by the forensic analysts?
A. This is to protect the staff and preserve any fingerprints that may need to be recovered at a later date
B. All forensic teams should wear protective latex gloves which makes them look professional and cool
C. Local law enforcement agencies compel them to wear latest gloves
D. It is a part of ANSI 346 forensics standard
Windows Security Event Log contains records of login/logout activity or other security- related events specified by the system's audit policy. What does event ID 531 in Windows Security Event Log indicates?
A. A user successfully logged on to a computer
B. The logon attempt was made with an unknown user name or a known user name with a bad password
C. An attempt was made to log on with the user account outside of the allowed time
D. A logon attempt was made using a disabled account
Event correlation is a procedure that is assigned with a new meaning for a set of events that occur in a predefined interval of time.
Which type of correlation will you use if your organization wants to use different OS and network hardware platforms throughout the network?
A. Same-platform correlation
B. Cross-platform correlation
C. Multiple-platform correlation
D. Network-platform correlation
Data Acquisition is the process of imaging or otherwise obtaining information from a digital device and its peripheral equipment and media
A. True
B. False
The following is a log file screenshot from a default installation of IIS 6.0.
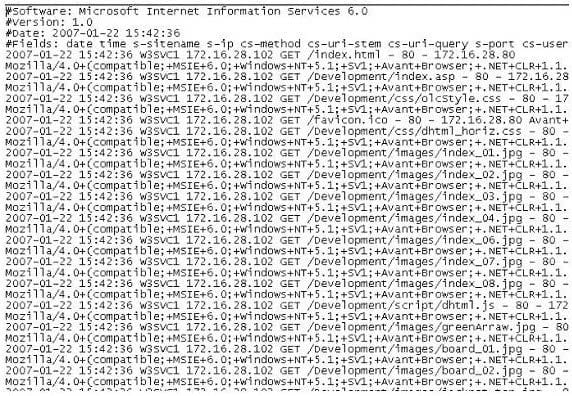
What time standard is used by IIS as seen in the screenshot?
A. UTC
B. GMT
C. TAI
D. UT
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
A. allinurl:"exchange/logon.asp"
B. intitle:"exchange server"
C. outlook:"search"
D. locate:"logon page"
You are running through a series of tests on your network to check for any security vulnerabilities. After normal working hours, you initiate a DoS attack against your external firewall. The firewall Quickly freezes up and becomes unusable. You then initiate an FTP connection from an external IP into your internal network. The connection is successful even though you have FTP blocked at the external firewall. What has happened?
A. The firewall failed-open
B. The firewall failed-closed
C. The firewall ACL has been purged
D. The firewall failed-bypass
What will the following command produce on a website login page?
SELECT email, passwd, login_id, full_name FROM members
WHERE email = '[email protected]';
DROP TABLE members; --'
A. Retrieves the password for the first user in the members table
B. This command will not produce anything since the syntax is incorrect
C. Deletes the entire members table
D. Inserts the Error! Reference source not found. email address into the members table
A Linux system is undergoing investigation. In which directory should the investigators look for its current state data if the system is in powered on state?
A. /auth
B. /proc
C. /var/log/debug
D. /var/spool/cron/

