300-915 Online Practice Questions and Answers
When trying to subscribe to an MQTT broker on the internet, the MQTT client is on a private subnet and must be NATed to reach the public broker.
What is the expected outcome when this configuration is in place?
A. The client periodically reconnects to the default gateway.
B. The client connects only once using the PENDING message to the broker.
C. The client periodically reconnects to the broker over the NAT connection.
D. The client connects only once using the CONNECT massage to the broker.
Which connector is southbound?
A. horizontal connector
B. cloud connector
C. device connector
D. universal connector
Which statement explains the correct position of a PLC within the CPwE architecture?
A. PLCs are always part of Level 0 ?process control.
B. PLCs are part of Level 4 ?site business planning.
C. PLCs are part of Level 1 ?basic control.
D. PLCs are placed at Level 2 ?area supervisory control.
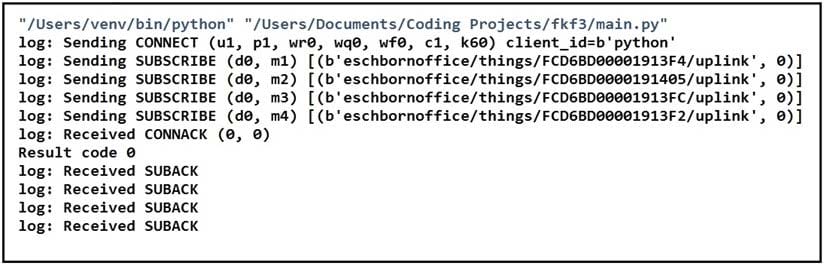
Refer to the exhibit. Which two statements about MQTT messaging are true? (Choose two.)
A. Result code 5 means the connection is accepted; result code 0 means the connection is "refused, not authorized".
B. Redundant ClientIDs are supported by MQTT brokers.
C. MQTT does not support a "keep alive" functionality because it runs on top of TCP.
D. Result code 0 means the connection is accepted; result code 5 means the connection is "refused, not authorized".
E. Brokers can send the Last Will and Testament messages on behalf of the client.
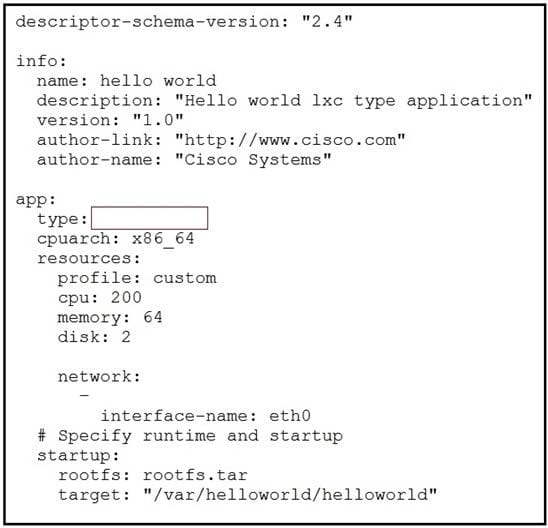
Refer to the exhibit. While troubleshooting an error on an application descriptor for a Docker app in Cisco IOx (package.yaml), the app type appears to be missing. Which app type must be added to the snippet to resolve the issue?
A. paas
B. docker-vm
C. docker
D. docker-app
The environment for an Industrial IoT project in a large open pit mine is being scoped. The location has a large amount of dust and the device will be exposed to less than 1 meter of water temporarily.
When the edge device is being chosen, which Ingress protection rating must be used?
A. IP37
B. IP61
C. IP67
D. IP76
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the REST API that is developed during the development of the software? (Choose two.)
A. Respond to request failures in detail to allow users for easier troubleshooting.
B. Implement HTTP whitelisting to only methods that are allowed.
C. Implement and review audit logs for security-related events.
D. Reject HTTP methods that are invalid with an error code 404.
E. Implement physical firewalling and access control to the resources.
Which two actions must be completed before starting the process of sending IoT data to the cloud via edge routers? (Choose two.)
A. Measure the voltage, power rating, and quiescent current for the sensors that send data to the cloud.
B. Gather the hardware (MAC) addresses of local and cloud routers to ensure low latency communication.
C. Collect information about the CPU architecture in the cloud and edge to ensure that they match.
D. Gather the interval, the volume, and the latency that the data must be provisioned with.
E. Collect information about growth, required elasticity, and high availability of the provisioning process.
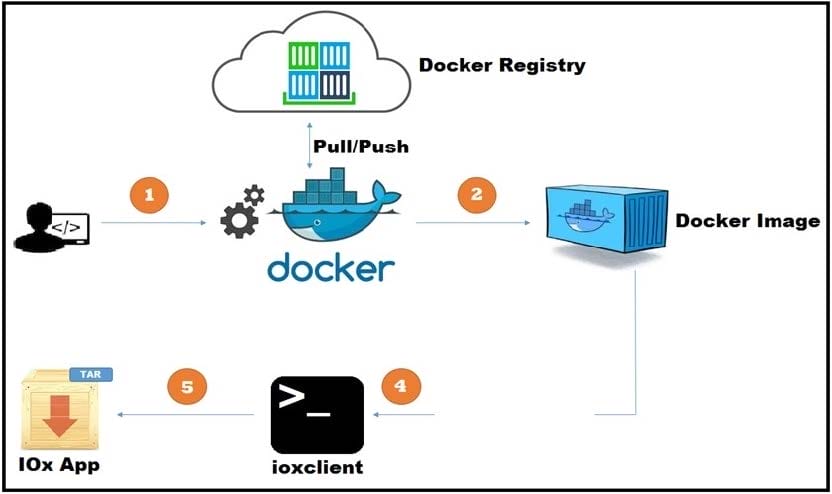
Refer to the exhibit. A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
A. Pull/push the image to the Docker registry.
B. Build the package.yaml files.
C. Build the package.cert file to sign the app.
D. Log in to device manager and load the application.
An IOx application is installed via Local Manager. Every time the application is started, it instantly stops.
Which troubleshooting steps should be taken?
A. There is something wrong with the application code itself.
B. Check the startup and entrypoint parameters.
C. Give the IOx application more CPU units.
D. Check local IOx settings, especially the network settings.

