300-725 Online Practice Questions and Answers
Which two sources provide data to Cisco Advanced Web Security Reporting to create dashboards? (Choose two.)
A. Cisco WSA devices
B. Cisco ISE
C. Cisco ASAv
D. Cisco Security MARS
E. Cisco Cloud Web Security gateways
What is the function of a PAC file on a Cisco WSA?
A. The file allows redirection of web traffic to a specific proxy server
B. The file is mandatory for a transparent proxy to redirect user traffic
C. The file provides instructions about which URL categories are permitted
D. The file is mandatory for an explicit proxy to forward user traffic
Which two modes of operation does the Cisco WSA provide? (Choose two.)
A. connector
B. proxy
C. transparent
D. standard
E. explicit
Which response code in the access logs indicates that a transaction was blocked due to policy?
A. TCP_DENIED/407
B. TCP_DENIED/401
C. TCP_DENIED/403
D. TCP_DENIED/307
Which two features on the Cisco WSA help prevent outbound data loss for HTTP or FTP traffic? (Choose two.)
A. web reputation filters
B. Advanced Malware Protection
C. third-party DLP integration
D. data security filters
E. SOCKS proxy
An administrator wants to restrict file uploads to Facebook using the AVC feature.
Under which two actions must the administrator apply this restriction to an access policy? (Choose two.)
A. Monitor Facebook General
B. Monitor Social Networking
C. Monitor Facebook Photos and Videos
D. Monitor Facebook Messages and Chat
E. Monitor Facebook Application
How does dynamic content analysis improve URL categorization?
A. It analyzes content based on cached destination content
B. It adds intelligence to detect categories by analyzing responses
C. It can be used as the only URL analysis method
D. It analyzes content of categorized URL to tune decisions and correct categorization errors
Which type of certificate must be installed on a Cisco WSA for HTTPS inspection?
A. server
B. client
C. root
D. wildcard
What is a benefit of integrating Cisco WSA with TrustSec in ISE?
A. The policy trace tool can be used to match access policies using specific SGT
B. Traffic of authenticated users who use 802.1x can be tagged with SGT to identification profiles in a Cisco WSA
C. ISE can block authentication for users who generate multiple sessions using suspect TCP ports
D. Users in a specific SGT can be denied access to certain social websites.
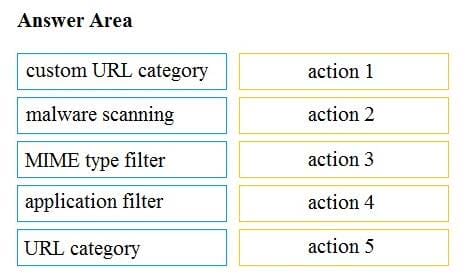
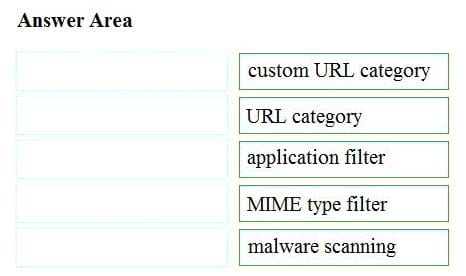
DRAG DROP
Drag and drop the Cisco WSA access policy elements from the left into the order in which they are processed on the right.
Select and Place: