300-710 Online Practice Questions and Answers
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
A. system support firewall-engine-debug
B. system support ssl-debug
C. system support platform
D. system support dump-table
Which function is the primary function of Cisco AMP threat Grid?
A. automated email encryption
B. applying a real-time URI blacklist
C. automated malware analysis
D. monitoring network traffic
Which function is the primary function of Cisco AMP threat Grid?
A. flood attack detection.
B. secure boot
C. image signing
D. DDoS mitigation
E. SYN flood detection
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10.10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format
that provides an adequate amount of addresses on the network.
What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
A. Delete and register the device to Cisco FMC.
B. Update the IP addresses from IPV4 to IPV6 without deleting the device from cisco FMC.
C. Format and register the device to Cisco FMC.
D. Cisco FMC does not support devices that use IPv4 IP addresses.
There is an increased amount of traffic on the network and for compliance reasons, management needs visibility into the encrypted traffic. What is a result of enabling TLS/SSL decryption to allow this visibility?
A. It prompts the need for a corporate managed certificate.
B. It will fail if certificate pinning is not enforced.
C. It has minimal performance impact.
D. It is not subject to any Privacy regulations.
Refer to the exhibit.
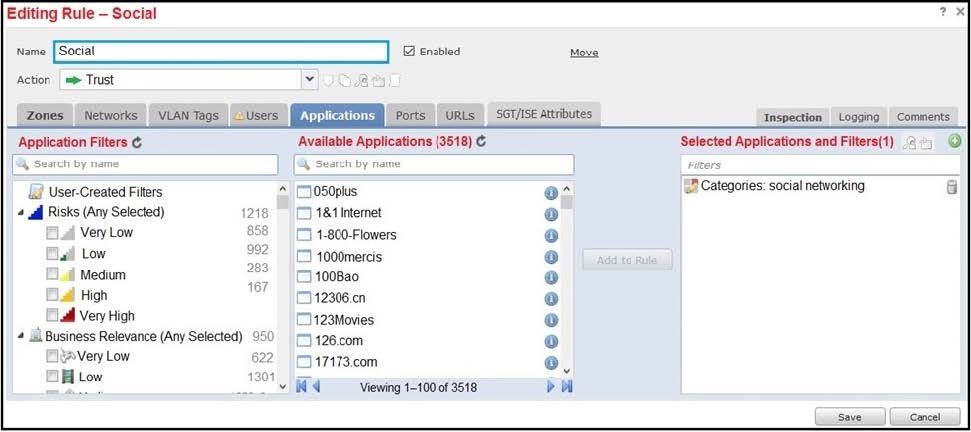
An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?
A. Add the social network URLs to the block list.
B. Change the intrusion policy to connectivity over security.
C. Modify the selected application within the rule.
D. Modify the rule action from trust to allow.
An engineer is creating an URL object on Cisco FMC. How must it be configured so that the object will match for HTTPS traffic in an access control policy?
A. Specify the protocol to match (HTTP or HTTPS).
B. Use the FQDN including the subdomain for the website.
C. Use the subject common name from the website certificate.
D. Define the path to the individual webpage that uses HTTPS.
A security engineer must configure policies tor a recently deployed Cisco FTD. The security policy for the company dictates that when five or more connections from external sources are initiated within 2 minutes, there is cause for concern. Which type of policy must be configured in Cisco FMC \z generate an alert when this condition is triggered?
A. application detector
B. access control
C. intrusion
D. correlation
A Cisco Secure Firewall Threat Defense device is configured in inline IPS mode to inspect all traffic that passes through the interfaces in the inline set. Which setting in the inline set configuration must be selected to allow traffic to pass through uninterrupted when VDB updates are being applied?
A. Tap Mode
B. Strict TCP Enforcement
C. Propagate Link State
D. Snort Fail Open
A software development company hosts the website https://dev.company.com for contractors to share code for projects they are working on with internal developers. The web server is on premises and is protected by a Cisco Secure Firewall Threat Defense appliance. The network administrator is worried about someone trying to transmit infected files to internal users via this site. Which type of policy must be able associated with an access control policy to enable Cisco Secure Firewall Malware Defense to detect and block malware?
A. SSL policy
B. file policy
C. network discovery policy
D. prefilter policy

