300-425 Online Practice Questions and Answers
A customer is concerned about mesh backhaul link security. Which level of encryption does the backhaul link use?
A. hash
B. AES
C. WEP
D. 3DES
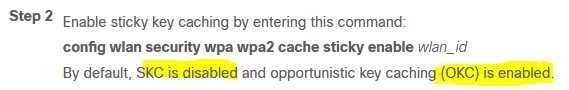
An engineer must ensure that the wireless network can accomplish fast secure roaming by way of caching keys on the access points. Which key caching mechanism is enabled by default on a Cisco AireOS WLC?
A. SKC
B. OKC
C. 802.11r
D. CCKM
A wireless engineer is performing a post verification of a wireless network. Which two metrics does the engineer verify to ensure that the wireless network can support voice services? (Choose two.)
A. The coverage area must have a noise floor that does not exceed-87 dBm.
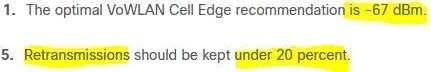
B. The client device must have at least an-67 dBm RSSI.
C. The rate of retransmitted packets must be 15 percent or below.
D. The rate of retransmitted packets must be 20 percent or below.
E. The client device must have at least an-65 dBm RSSI.
When conducting a site survey for real-time traffic over wireless, which two design capabilities of smartphones and tablets must be considered? (Choose two.)
A. no support for 802.11ac
B. higher data rates than laptops
C. fewer antennas than laptops
D. no support for 802.11r
E. lower data rates than laptops
An enterprise network administrator is asked to set up an experimental WLAN for a collaboration project with a local service provider. The WLAN must be anchored to a WLC in the service provider data center using legacy mobility mode. After the configurations are completed on the WLCs and the firewalls in the path, the data path mobility tunnel is failing to come up. What should be performed by the administrator to debug the issue?
A. Establish a Telnet connection from a local PC to the firewall on port 97.
B. Use the eping command on the WLC.
C. Establish a Telnet connection from a local PC to the firewall on port 16666.
D. Use the mping command on the WLC.
Refer to the exhibit.
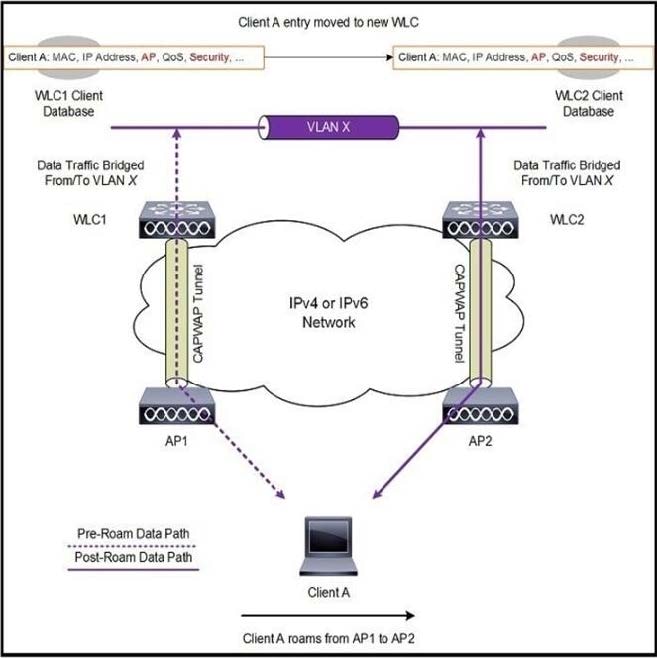
Client A is roaming from AP1 on WLC1 to AP2 on WLC2. The client roams between two APs registered to two different controllers. The WLAN on the two controllers is on a different subnet. Which scenario explains the client's roaming behavior?
A. The client database entry is different than that of Layer 2 roam. (Instead of copying, it moves the database to the new controller.)
B. The client database entry is different than that of Layer 2 roam. (Instead of moving, it copies the database to the new controller.)
C. The client database entry is different than that of Layer 2 roam because the client database is neither moved nor copied into the new controller.
D. The client database remains in the mobility anchor controller and it is not copied or moved.
An engineer is working for a manufacturing company that has a centralized deployment model. Guests at headquarters need wireless access for presentations, demonstrations, and sharing of information. The engineer must provide external users with secure guest access by connecting to anchor controllers on the DMZ. Auto-Anchor Mobility has been selected in the mobility group to accomplish it. Both anchors are configured as part of the mobility group for HQ. Which design approach ensures that clients connect to the primary controller first and are pushed to the secondary if the primary fails?
A. Set the Anchor priority for the primary controller to 1.
B. Set the Anchor priority for the secondary controller to 1.
C. Configure ECMP but weigh the cost to be higher to go to the primary.
D. Configure ECMP but weigh the cost to be higher to go to the secondary.
An architect configures a set of AirOS controllers to be in the same mobility group as the existing controllers. The implementation should facilitate inter-controller roaming for users in their new campus. After the configuration, the mobility tunnel is not operational for the data path in the network. Which two validations should be performed? (Choose two.)
A. firewall port 16666
B. mping
C. eping
D. rping
E. firewall IP protocol 97
An engineer must design AP placements for a new branch office that contains two floors. The engineer uses Ekahau to complete the predictive survey. To calculate the signal bleed through between floors, the engineer creates a building, adds the floors, and attenuations areas. After the scale is set, what else must be added on the floors to accurately measure the signal bleed at a specific location?
A. Choose the access point models.
B. Start the auto planner.
C. Add alignment points.
D. Draw in coverage areas.
A network engineer is working for an enterprise where most of the laptops support 802.11v. To optimize the client roaming experience, configuration changes must be made on the corporate SSID to force clients to use the best APs based on the 802.11 v BSS transition message. Which configuration meets this requirement?
A. Enable BSS transition for the SSID and disable dissociation imminent to avoid client disconnects.
B. Enable the BSS transition option with an optimized roaming timer for the corporate SSID.
C. Enable coverage hole detection and BSS transition and disable dissociation imminent.
D. Disable coverage hole detection and enable 802.11k for the corporate SSID.