2V0-641 Online Practice Questions and Answers
Which two statements are valid regarding vCloud Networking and Security (vCNS) and NSX? (Choose two.)
A. Both vCNS and NSX support multiple hypervisor environments.
B. NSX provides support for multiple hypervisor environments, vCNS does not.
C. Both vCNS and NSX support dynamic routing protocols.
D. NSX supports dynamic routing protocols, vCNS does not.
Which VMware NSX for vSphere component can be created on-demand using vRealize Automation?
A. The logical switch
B. The logical distributed router
C. The distributed firewall
D. The NSX Edge Services Gateway
Which two statements are true regarding NSX? (Choose two.)
A. Workloads can be placed and moved independently of physical topology.
B. Operational efficiency can be achieved through automation of the physical network.
C. Workload deployments are non-disruptive over the existing physical network.
D. NSX implementation requires a VMware vSphere environment.
Which two statements are true regarding NSX High Availability (HA)? (Choose two.)
A. NSX HA is configured as Active-Active.
B. NSX HA is configured as Active-Standby.
C. If an Active node fails, there is no service interruption during failover.
D. If an Active node fails, there is a 15 second service interruption during failover.
-- Exhibit -
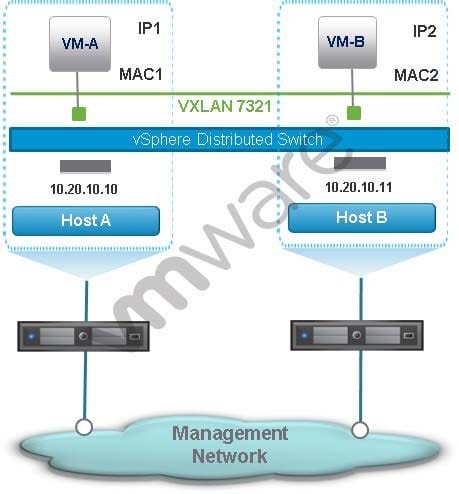
-- Exhibit -An NSX administrator creates the NSX network in the exhibit.
What destination IP address will Host-A use when sending a VXLAN frame to Host-B?
A. The IP address of one of Host-B's new vmkernel ports created during host configuration.
B. The IP address of Host-B's management vmkernel port, which is also the VTEP IP address.
C. The IP address of Host-B's NSX Controller. The NSX Controller forwards the VXLAN frame to Host-
D. The IP address Host-B provided to Host-A during VXLAN tunnel setup negotiations.
Which is not a valid Destination option for a General Logical Firewall rule?
A. Datacenter
B. Virtual App
C. MAC Set
D. Network
Which Virtual Machine cannot be protected by the Distributed Firewall?
A. A Virtual Machine connected to a vDS Portgroup running on an ESXi 5.1 host.
B. A Virtual Machine connected to a vSS Portgroup running on an ESXi 5.5 host.
C. A Virtual Machine connected to a vDS Portgroup running on an ESXi 5.5 host.
D. A Virtual Machine connected to a logical switch running on an ESXi 5.1 host.
Which two options are valid SpoofGuard operational modes? (Choose two.)
A. Allow Local Address as Valid Address in This Namespace
B. Allow and Approve DHCP Requests Regardless of Enabled Mode
C. Automatically Trust IP Assignments on Their First Use
D. Manually Inspect and Approve All IP Assignments Before Use
What is required before running an Activity Monitoring report?
A. Enable data collection on the NSX Controller.
B. Enable data collection on the vCenter Server.
C. Enable data collection on the NSX Manager.
D. Enable data collection on the virtual machine.
-- Exhibit -
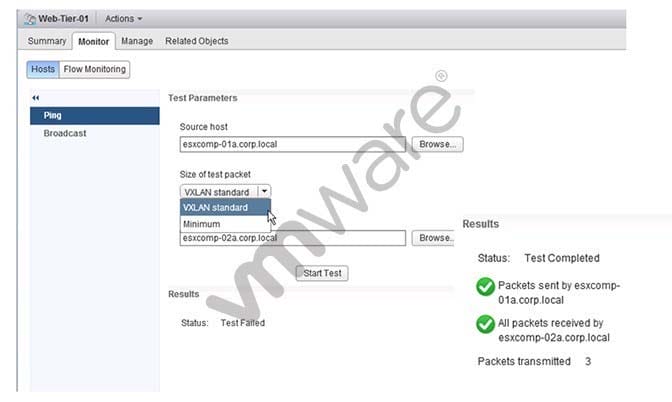
-- Exhibit -
An administrator is testing connectivity between two ESXi hosts and uses the ping utility, as shown in the
Exhibit.
Based on the results shown in the exhibit, which statement is correct?
A. Communication between the hosts is working correctly.
B. The hosts are in separate subnets.
C. The MTU size is too small.
D. A logical router has not been deployed and configured.

