2V0-21.23 Online Practice Questions and Answers
Refer to the exhibit.
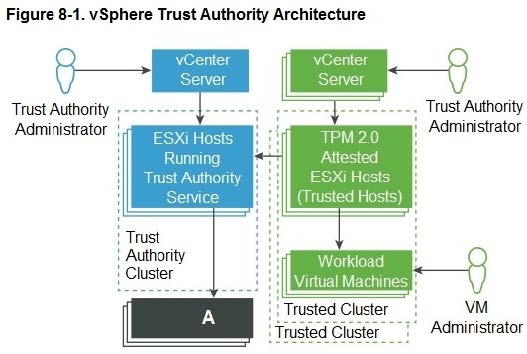
Which trusted infrastructure component is missing and represented by the area labeled "A"? (Choose the best answer.)
A. Key Management Server
B. vSphere Virtual Machine Encryption
C. Key Provider Service
D. Attestation Service
In a vSphere High Availability (vSphere HA) cluster, which condition can be detected by datastore heartbeating? (Choose the best answer.)
A. Fault tolerance virtual machine (VM) failover
B. Network isolation
C. Virtual machine (VM) disk failure
D. Datastore All Paths Down (APD) event
Which solution can be used to automatically deploy a fully configured VMware software-defined data center (SDDC)? (Choose the best answer.)
A. vCenter Server
B. vRealize Suite
C. vSphere Lifecycle Manager
D. VMware Cloud Foundation
In a vSphere High Availability (vSphere HA) cluster, which action does vSphere HA take when the VM Monitoring service does NOT receive heartbeats from a virtual machine (VM) in the cluster? (Choose the best answer.)
A. The VM is restarted on a different host in the cluster.
B. The VM is suspended on the same host in the cluster.
C. The VM is migrated to a different host in the cluster.
D. The VM is restarted on the same host in the cluster.
An administrator is investigating the reason for a virtual machine restarting. In the vmware.log file, the administrator finds the following error:
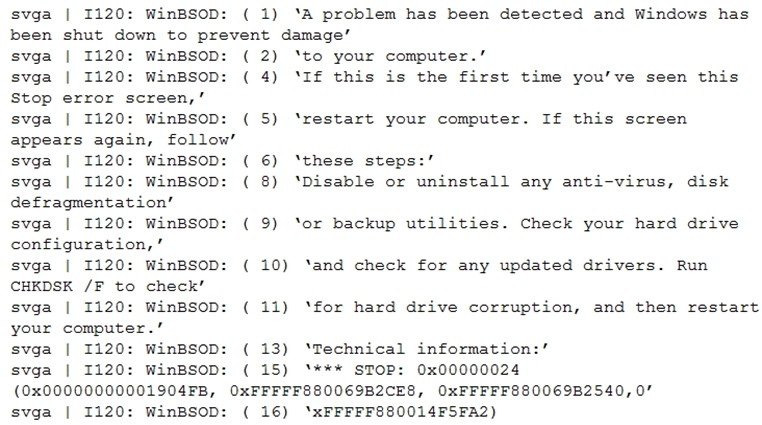
What is a likely cause of this virtual machine restart? (Choose the best answer.)
A. Guest operating system fault
B. User or API request to shut down guest operating system
C. High Availability
D. User or API request to restart guest operating system
An administrator is tasked with configuring vSphere Trust Authority. The administrator has completed the following steps:
Set up the workstation Enabled the Trust Authority Administrator Enabled the Trust Authority State Collected information about the ESXi hosts and vCenter to be trusted
Which step does the administrator need to complete next?
A. Import the Trusted Host information to the Trust Authority Cluster
B. Import the Trusted Cluster information to the Trusted Hosts
C. Create the Key Provider on the Trusted Cluster
D. Import the Trusted Host information to the Trusted Cluster
An administrator is tasked with migrating a single virtual machine (VM) from an existing VMware vCenter to a secure environment where corporate security policy requires that all VMs be encrypted. The secure environment consists of a dedicated vCenter instance with a 4-node vSphere cluster and already contains a number of encrypted VMs.
Which two steps must the administrator take to ensure the migration is a success? (Choose two.)
A. Ensure that the source and destination vCenter instances share the same Key Management Server (KMS).
B. Ensure that Encrypted vMotion Is turned off for the VM.
C. Ensure that the VM is encrypted before attempting the migration.
D. Ensure that the VM is powered off before attempting the migration.
E. Ensure that the source and destination vCenter Servers have a different Key Management Server (KMS).
An administrator is tasked with allowing a single user the ability to take snapshots on a virtual machine. When looking in vCenter, the administrator can see that there are already users and groups assigned permissions on the virtual machine as follows:
The group VMJJsers has the Virtual Machine Power User role. The group VM_Viewers has the Read Only role.
The administrator confirms that the user requesting the additional access is currently one of five members of the VM_Viewers group
Which two steps should the administrator take to grant this user the additional access required without impacting the user access of others? (Choose two.)
A. Add the user to the VM_Users group and leave the permissions on the virtual machine object unchanged
B. Add a new permission on the virtual machine object selecting the user and the new custom role.
C. Edit the Read Only role to add the Virtual Machine Snapshot Management privileges.
D. Create a new custom role with the Virtual Machine Snapshot Management privileges.
E. new permission on the virtual machine object selecting the VM_Viewers group and the new custom
An administrator has a requirement to revert a running virtual machine to a previous snapshot after a failed attempt to upgrade an application. When the administrator originally took the snapshot, the following choices in the Take Snapshot dialog were made:
Snapshot the virtual machine's memory = false Quiesce guest file system = false
What will be the result of the administrator selecting the `Revert to Latest Snapshot? option to return the virtual machine to a previous snapshot? (Choose two.)
A. The virtual machine will be restored to the parent snapshot
B. The virtual machine will be restored in a powered off state
C. The virtual machine will be restored to the child snapshot
D. The virtual machine will be restored in a powered on state
E. The virtual machine will be restored in a suspended state
What are two uses cases for VMware Tools? (Choose two.)
A. Time synchronization with an NTP server
B. Direct deployment of the Aria Automation Config minion
C. Share folders between ESXi hosts and guest OS file systems
D. Ability to shut down a virtual machine remotely
E. Support for unsupported network device drivers

