210-255 Online Practice Questions and Answers
Which option can be addressed when using retrospective security techniques?
A. if the affected host needs a software update
B. how the malware entered our network
C. why the malware is still in our network
D. if the affected system needs replacement
Refer to the exhibit. What can be determined from this ping result?
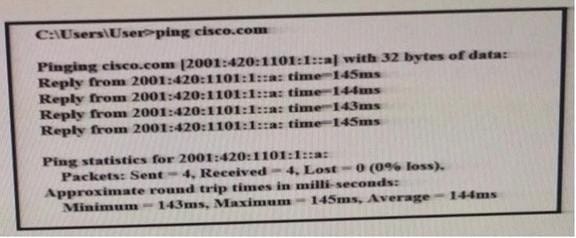
A. The public IP address of cisco.com is 2001:420:1101:1::a.
B. The Cisco.com website is down.
C. The Cisco.com website is responding with an internal IP.
D. The public IP address of cisco.com is an IPv4 address.
Which option is generated when a file is run through an algorithm and generates a string specific to the contents of that file?
A. URL
B. hash
C. IP address
D. destination port
According to NIST-SP800-61R2, which option should be contained in the issue tracking system?
A. incidents related to the current incident
B. incident unrelated to the current incident
C. actions taken by nonincident handlers
D. latest public virus signatures
How is confidentiality defined in the CVSS v3.0 framework?
A. confidentiality of the information resource managed by person due to an unsuccessfully exploited vulnerability
B. confidentiality of the information resource managed by a person due to a successfully vulnerability
C. confidentiality of the information resources managed by a software component due to a successfully exploited vulnerability
D. confidentiality of the information resource managed by a software component due to an unsuccessfully exploited vulnerability
When incident data is collected, it is important that evidentiary cross-contamination is prevented. How is this accomplished?
A. by allowing unrestricted access to impacted devices
B. by not allowing items of evidence to physically touch
C. by ensuring power is removed to all devices involved
D. by not permitting a device to store evidence if it is the evidence itself.
Which two statements correctly describe the victim demographics section of the VERIS schema? (Choose two.)
A. The victim demographics section describes but does not identify the organization that is affected by the incident.
B. The victim demographics section compares different types of organizations or departments within a single organization.
C. The victim demographics section captures general information about the incident.
D. The victim demographics section uses geolocation data to identify the organization name of the victim and the threat actor.
Which netstat command show ports? (Choose two)
A. netstat a
B. netstat -l
C. netstat -v
D. netstat -g
According to NIST-SP800-61R2, why is it important to keep clocks synchronized?
A. event correlation
B. to link with other countries easily
C. to not lose track of time
D. to measure the effectiveness of an attack
Which technology generates events utilizing proxy logs?
A. Firepower
B. Email Security Appliance
C. Stealthwatch
D. Web Security Appliance

