1Z0-1104-22 Online Practice Questions and Answers
Which volume type contains the image used to boot a compute instance?
A. Init 6 volume
B. Boot volume
C. Startup volume
D. Block volume
Select the component that encompasses the overall configuration of your WAF service on OCI.
A. Protection rules
B. Bot Management
C. Web Application Firewall policy
D. Origin
Which is NOT a compliance document?
A. Certificate
B. Penetration test report
C. Attestation
D. Bridge letter
Which statement is true about origin management in WAF?
Statement A: Multiple origins can be defined.
Statement B: Only a single origin can be active fora WAF.
A. Only statement B is true.
B. Both the statements are false.
C. Both the statements are true.
D. Only statement A is true.
As a security architect, how can you preventunwanted bots while desirable bots are allowed to enter?
A. Data Guard
B. Vault
C. Compartments
D. Web Application Firewall (WAF)
What are the security recommendations and best practices for Oracle Functions?
A. Grant privileges to UID and GID 1000, such that the functions running within a container acquire the default rootcapabilities.
B. Add applications to network security groups for fine-grained ingress/egress rules.
C. Define a policy statement that enables access to functions for requests coming from multiple IP addresses.
D. Ensure that functions in a VCN have restricted access to resources and services.
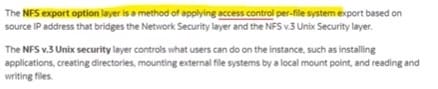
A company has OCI tenancy which has mount target associated with two File Systems, CG_1 and CG_2. These FileSystems are accessed by IP-based clients AB_1 and AB_2 respectively. As a security administrator, how can you provide access to both clients such that CGI has Read only access on AB1 and CG_2 has Read/Write access on AB_2?
A. NFS Export Option
B. Access Control Lists
C. NFS v3 Unix Security
D. Vault
Which statement is true about using custom BYOI instances in Windows Servers that are managed by OS Management Service?
A. Windows Servers that does not have the minimum agent version does not require an agent update or installation.
B. Windows Servers that already has the minimum agent version does not require an agent update or installation.
C. Windows Servers that already has the minimum agent version requires an agent update or installation.
D. Windows Servers that does not have the minimum agent version requires an agent update or installation.
Which of these protects customer data at rest and in transit in a way that allows customers to meet their security and compliance requirements forcryptographic algorithms and key management?
A. Security controls
B. Customer isolation
C. Data encryption
D. Identity Federation
What is the use case for Oracle cloudinfrastructure logging analytics service?
A. monitors, aggregates, indexes and analyzes all log data from on-premises.
B. labels data packets that pass through the internet gateway
C. automatically create instances to collect logs analysis and send reports
D. automatically and manage any log based on a subscription model