1V0-81.20 Online Practice Questions and Answers
Refer to the exhibit.
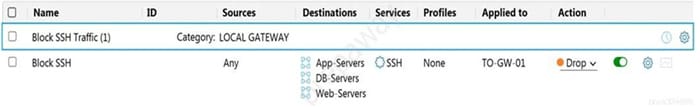
Which statement is true about the firewall rule?
A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
B. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that rejects traffic on port 22
C. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that drops traffic on port 22
D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
Which of the following is true about VMware Carbon Black Cloud Enterprise EDR watchlists?
A. They only update annually
B. You cannot customize them
C. They are made up of reports
D. Each watchlist is user specific
Which would require a Layer 7 Firewall?
A. block a specific port
B. block a subnet range
C. block a host
D. block a specific application
What is the safe course of action for a USB disk of unknown ownership and origin?
A. Do not connect the USB to any computer as it may be a USB Killer device
B. Connect the USB device to your computer and allow the DLP software to protect it
C. Connect the USB to a non-Windows device and examine it
D. Connect the USB to an air gapped system and examine it
When you share a report in Workspace One Intelligence with a specified user, how is the report shared?
A. Desktop Notification
B. Console Message
C. SMS
D. Email
Micro segmentation is under which pillar of trust in VMware's 5 pillars of Zero Trust?
A. User
B. Session/Transport
C. Application
D. Device
What is the term used to describe a type of social engineering attack aimed at a specific person or specific type of person?
A. Phishing
B. Whaling
C. Tailgating
D. Spear Phishing
What is a unique benefit of Next Generation Antivirus over standard Antivirus?
A. signature based heuristics
B. predictive analytics
C. file based heuristics
D. reactive analytics
An organization using VMware Carbon Black makes use of an unsigned third party application that is critical to business function. Unfortunately, the application has a reputation of Potentially Unwanted Program and is prevented from running based on the policy.
What Approved list mechanism will allow this application to run in your environment while maintaining the most secure posture?
A. MD5 Hash based
B. Certs based
C. IT Tools based
D. SHA-256 Hash based
Which three are VMware Workspace ONE SDK capabilities? (Choose three.)
A. data loss prevention
B. find my device
C. single sign-on
D. geofencing
E. application blacklist

