1D0-571 Online Practice Questions and Answers
Which of the following is the most likely first step to enable a server to recover from a denial-of- service attack in which all hard disk data is lost?
A. Enable virtualization
B. Contact the backup service
C. Contact a disk recovery service
D. Rebuild your RAID 0 array
You purchased a network scanner six months ago. In spite of regularly conducting scans using this software, you have noticed that attackers have been able to compromise your servers over the last month. Which of the following is the most likely explanation for this problem?
A. The network scanner needs to be replaced.
B. The network scanner is no substitute for scans conducted by an individual.
C. The network scanner has atrojan.
D. The network scanner needs an update.
What is the primary use of hash (one-way) encryption in networking?
A. Signing files, for data integrity
B. Encrypting files, for data confidentiality
C. Key exchange, for user authentication
D. User authentication, for non-repudiation
Which of the following will best help you ensure a database server can withstand a recently discovered vulnerability?
A. Updating the company vulnerability scanner and conducting a new scan
B. Adding a buffer overflow rule to the intrusion detection system
C. Reconfiguring the firewall
D. Installing a system update
Which of the following standards is used for digital certificates?
A. DES
B. Diffie-Hellman
C. X.509
D. RC5
A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset:
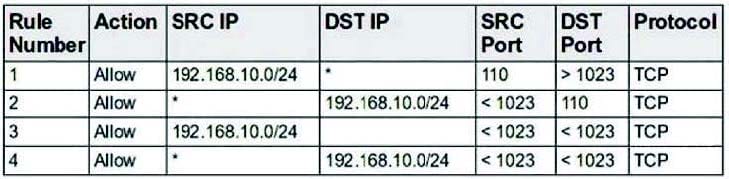
Which choice describes the next step to take now that this ruleset has been enabled?
A. From the internal network, use your Web browser to determine whether all internal users can access the Web server.
B. From the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
C. From the external network, use your Web browser to determine whether all external users can access the Web server.
D. From the external network, use your e-mail client to determine whether all external users can access the e-mail server.
You want to create a quick solution that allows you to obtain real-time login information for the administrative account on an LDAP server that you feel may become a target. Which of the following will accomplish this goal?
A. Reinstall the LDAP service on the server so that it is updated and more secure.
B. Install an application that creates checksums of the contents on the hard disk.
C. Create a login script for the administrative account that records logins to a separate server.
D. Create a dummy administrator account on the system so that a potential hacker is distracted from the
real login account.
Which tool is best suited for identifying applications and code on a Web server that can lead to a SQL injection attack?
A. A vulnerability scanner
B. A packet sniffer
C. An intrusion-detection system
D. A network switch
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
A. Authentication databases, including directory servers
B. Intrusion detection systems, especially those placed on sensitive networks
C. Log files on firewall systems
D. Firewall settings for desktop systems
You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
A. Firewall
B. Intrusion-detection system
C. Camera
D. Security guard

