156-915.77 Online Practice Questions and Answers
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server and backups of your Security Management Server. What is the correct procedure for rebuilding the Gateway quickly?
A. Reinstall the base operating system (i.e., GAiA). Configure the Gateway interface so that the Gateway can communicate with the TFTP server. Revert to the stored snapshot image, and install the Security Policy.
B. Run the command revert to restore the snapshot, establish SIC, and install the Policy.
C. Run the command revert to restore the snapshot. Reinstall any necessary Check Point products. Establish SIC and install the Policy.
D. Reinstall the base operating system (i.e., GAia). Configure the Gateway interface so that the Gateway
can communicate with the TFTP server. Reinstall any necessary Check Point products and previously applied hotfixes. Revert to the stored snapshot image, and install the Policy.
What is the officially accepted diagnostic tool for IP Appliance Support?
A. ipsoinfo
B. CST
C. uag-diag
D. cpinfo
How can you check whether IP forwarding is enabled on an IP Security Appliance?
A. clish -c show routing active enable
B. cat /proc/sys/net/ipv4/ip_forward
C. echo 1 > /proc/sys/net/ipv4/ip_forward
D. ipsofwd list
You cannot use SmartDashboard's User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
A. 1, 2, and 3
B. 2 and 3
C. 1 and 2
D. 1 and 3
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
A. John should install the Identity Awareness Agent
B. The firewall admin should install the Security Policy
C. John should lock and unlock the computer
D. Investigate this as a network connectivity issue
What type of traffic can be re-directed to the Captive Portal?
A. SMTP
B. HTTP
C. All of the above
D. FTP
Fill in the blank.
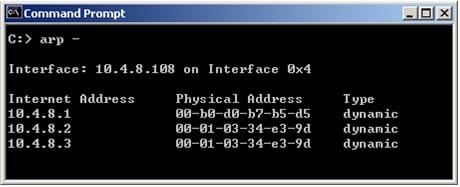
In New Mode HA, the internal cluster IP VIP address is 10.4.8.3. An internal host 10.4.8.108 successfully pings its Cluster and receives replies. Review the ARP table from the internal Windows host 10.4.8.108. Based on this information, what is the active cluster member's IP address?
A. 10.4.8.2
Type the full cphaprob command and syntax that will show full synchronization status.
A. cphaprob -i list
When, during policy installation, does the atomic load task run?
A. It is the first task during policy installation.
B. It is the last task during policy installation.
C. Before CPD runs on the Gateway.
D. Immediately after fwm load runs on the Smart Center.
The process ________ is responsible for Management High Availability synchronization.
A. CPLMD
B. FWM
C. Fwsync
D. CPD

